As a software engineer for more than 20 years, I have seen how computing has evolved since the beginning of internet age. A couple of months back, I heard one of my seniors passionately speak about his computing experience from the 80s that evoked my curiosity on early computer revolution. My search for an authority on this topic ended with the best-selling book by Steven Levy about hacker culture published in 1984 – Hackers: Heroes of the Computer Revolution.

The intriguing element of the book is “Hacker Ethic” – in Steven’s words, it was a philosophy of sharing, openness, decentralization and getting your hands on machines at any cost to improve the machines and to improve the world. He narrates computer evolution from mid 1950s till 1984 from a hacker perspective, covering people and machines that might not be well known to people from the internet age.
For software engineers of current millennium who take CPU speed at gigahertz and memory at terabytes for granted in 64-bit machines, it is unfathomable that predecessors from this hacker era created wonders with a tiny fraction of these resources in 8-bit machines. Assembly language programmers were a celebrated lot and they innovated by hacking primitive microprocessor-based computers with machine language!
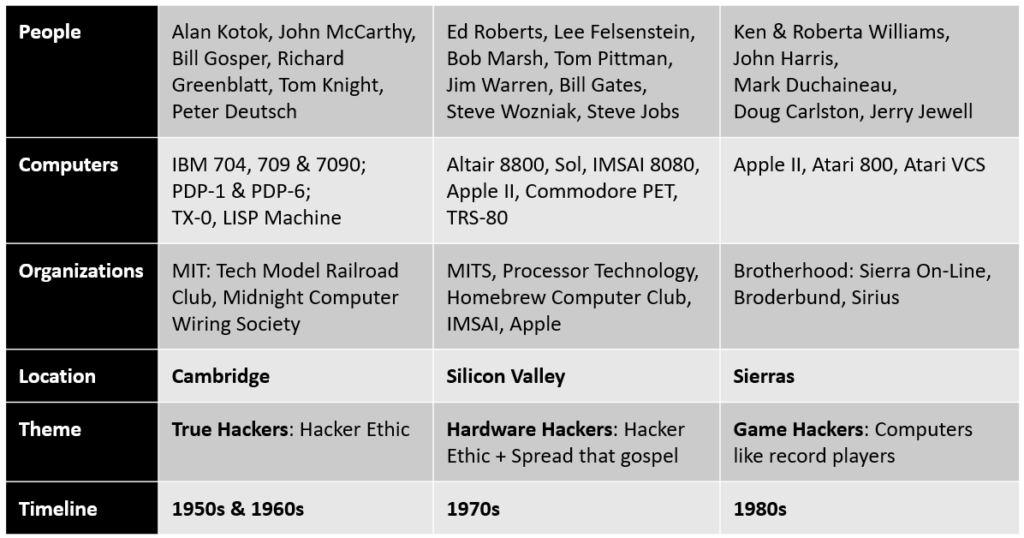
Steven explains how “Hacker Ethic” evolved over three decades starting from the closed community of early mainframe hackers on time share terminals at MIT, to the open community of self-made hardware hackers out of their garages at Silicon Valley, finally paving the way for game hackers. This forms the three parts of the book that I have summarized in the picture below.
I have watched several videos on personal computing revolution and particularly enjoyed Triumph of the Nerds. But reading a book is always a unique experience as it gives an opportunity for imagination. As I read this book, I felt as if I was sitting beside the hackers and watching them code. While computing has changed a lot over generations, one aspect has remained just the same – hackers always push computers to the limits and their hunger for more has driven the industry forward!